DHS Form 10008 APPLICATION FOR SAFETY ACT DESIGNATION
Support Anti-terrorism by Fostering Effective Technologies Act of 2002
10008_Application_for_SAFETY_Act_Designation
OMB: 1640-0001
OMB Control No. 1640-0001 Expires: 03/31/2016
Department of Homeland Security
Science and Technology Directorate
APPLICATION FOR SAFETY ACT DESIGNATION
The purpose of completing a SAFETY Act Designation application is for you, the Seller of a Technology, to explain to the Department how your Technology qualifies for the system of risk management and litigation management under the SAFETY Act. The questions are designed to elicit the information that will allow the Department to understand exactly what it is that you sell and how it relates to the criteria for Designation set forth in the Act. Not all questions will be applicable to all types of technology – this is unavoidable given the broad range of potential types of qualifying technologies. If a particular request or question does not seem relevant to your Technology, explain why you do not think it is relevant in your response to that item. In addition, the Department will accept any supplemental information regarding your Technology that you wish to provide. It is particularly important to identify any prior use or ongoing procurements of your Technology by the military, Federal Government agencies, or State, local, or foreign governmental entities. Prior Government use or procurement may significantly expedite the application process.
(Designation Application Form on following page)
Privacy Act Notice: DHS Authority to Collect This Information: 6 U.S.C. §§ 441–444 (the “SAFETY Act”) and 6 C.F.R. Part 25, 71 Fed. Reg. 33147, 33159. Principal Purposes: DHS collects telephone numbers, addresses, and other identifying information for the purpose of contacting individuals seeking liability protections on issues related to the SAFETY ACT application process. Routine Uses and Sharing: In general, DHS will not use this information for any purpose other than DHS personnel contacting the individual. However, DHS may release this information of an individual on a case-by-case basis as described in the S&T SAFETY Act System of Records Notice (SORN), which can be found at: www.dhs.gov/privacy. Disclosure: Submission of this information is voluntary and an individual may opt not to provide the requested information or to provide only some of the information DHS requests. If an individual chooses to opt not to provide some or all of the requested information, DHS may not be able to process the individual’s request.
PRA Burden Statement: An agency may not conduct or sponsor an information collection and a person is not required to respond to this information collection unless it displays a current valid OMB control number and an expiration date. The control number for this collection is 1640- 0001 and this form will expire on 03/31/2013. The estimated average time to complete this form is 80 hours per respondent. If you have any comments regarding the burden estimate you can write to Department of Homeland Security, Science and Technology Directorate, Washington, DC 20528.
DHS Form 10008 (10/06)
Application for SAFETY Act Designation
APPLICATION TYPE

 D1. Type
of Application.
This
application
is
a(n)
(choose
one):
Initial
Filing
D1. Type
of Application.
This
application
is
a(n)
(choose
one):
Initial
Filing
Application following a Pre-Application Consultation
 Application
ID #:
Resubmission
of a
Previous Application
Application
ID #:
Resubmission
of a
Previous Application
Application ID #:
 Application
for Renewal of
Designation:
Application
for Renewal of
Designation:
Application ID #:
D1.1 Public Web site Listing
If your Technology is awarded SAFETY Act coverage, you have the opportunity to be listed on the SAFETY Act Web site as a Designated Seller of a Qualified Anti-Terrorism Technology (QATT). [For example, if you apply for Designation and Certification and receive Designation, your Technology will be listed under Designated Technologies. Or, if you are granted DT&E Designation, regardless of which protection you applied for, you will be so listed on the Web site. Note: By statute, all Certified Technologies will be displayed in the Approved Products List for Homeland Security on the Web site.]
 I
wish to
have my QATT listed
on the
public Web site under the
appropriate
classification.
I
wish to
have my QATT listed
on the
public Web site under the
appropriate
classification.
 I
do not wish to
have my QATT listed on
the public
Web site
under the
appropriate
classification.
I
do not wish to
have my QATT listed on
the public
Web site
under the
appropriate
classification.
EXPEDITED REVIEW
D2. Request for Expedited Review
In its discretion, the Department may identify categories of anti-terrorism technologies for which expedited processing may be granted. For example, the Under Secretary may conduct expedited processing for applications that are the subject of a pending Federal, State, or local procurement, that address a particular threat, that involve particular types of anti-terrorism technologies, or for other reasons. If you are requesting expedited review, please specify the basis for such a request, including, if applicable, information concerning an ongoing procurement. Such information should include the following:
The name of procuring organization;
Contact information for relevant Government procurement officials;
The related Request for Proposal (RFP) number or other official identifier of the procurement, if available; and
Upcoming deadlines relating to the procurement (e.g., submission deadline, decision/contract award, etc.).
Please note if your application falls under a published DHS Notice of Expedited Processing, provide the reference number for such Notice, and a brief statement as to why your application falls within the scope of the Notice. If you wish to provide other bases for expedited processing, please specify.
REGISTRATION INFORMATION
D3. Registration Status (choose one):
 My
initial Seller registration
is included
with this
application.
My
initial Seller registration
is included
with this
application.

 I
am updating or
correcting previous
registration
information.
My previously
provided registration
information
is still
accurate.
I
am updating or
correcting previous
registration
information.
My previously
provided registration
information
is still
accurate.
D3.1. Seller Name:
OVERVIEW OF THE ANTI-TERRORISM TECHNOLOGY
D4. Non-proprietary Summary
D4.1. Name of your Technology:
D4.2. Company and Technology Description. Provide an overview of your company, including business structure, place of incorporation, company history, a description of your business, and a brief, two-line description of the Technology that is the subject of this application. This description of your Technology should be non-proprietary, that is, appropriate for public viewing on the SAFETY Act website if approved for SAFETY Act coverage.
D5. Summary of your Technology. Please provide a brief (no more than two-page) overall description of your Technology. If your Technology is a product or device, please describe the Technology, including its principal elements, subsystems and components. If your Technology is a service, please provide an overview of the nature of the service, the actions, activities, planning, training, and/or expertise involved in providing the service and how the service is designed to counter terrorist threats. If your Technology is an “integrator” of various products,
services, or legacy systems, indicate how the Technology will integrate the various component parts.
D6. Past Sales and ongoing procurements. Note: It may be very important and could significantly expedite your application if your Technology has been acquired or used (or is subject to an ongoing procurement) by the military, a Federal Government agency, or a State, local or foreign governmental entity.
D6.1. Who has purchased or plans to purchase your Technology? (Choose all that apply.) Please provide a brief description of such purchases.




 Federal
Government
(Agency: Approximate
Date: ) State
Government (State: Approximate
Date: ) Local
Government
(City/County: Approximate
Date: ) Commercial
organization (Name: Approximate
Date: ) Foreign
Government
(Name: Approximate
Date: )
Federal
Government
(Agency: Approximate
Date: ) State
Government (State: Approximate
Date: ) Local
Government
(City/County: Approximate
Date: ) Commercial
organization (Name: Approximate
Date: ) Foreign
Government
(Name: Approximate
Date: )
D6.2. Contact information. Include name, address, phone number, and e-mail address or procuring officials, if available. If POCs are provided as sources of information or testimonials, check below to indicate that you have contacted
them and that they are expecting to hear from DHS related to your Technology. Also, indicate below what information we should expect from each POC.
 The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
D6.3. If applicable, provide information regarding your Technology’s use by the United States Government or by any State, local, or foreign Government.
D6.4. Please identify any determination made by Federal, State, or local Government officials in any past or ongoing procurement or other context that your Technology is appropriate for the purpose of countering terrorism.
D7. If any other corporate entity or entities should be identified as an authorized Seller of the subject Technology in addition to the firm identified in the response to D3.1 above, please identify each entity and the place in which it is organized.
D8. Provide the earliest date of sale of the Technology for which you are requesting SAFETY Act coverage. This should represent the date that the Technology was first deployed, used or modified to be used in an Anti-terrorism context. Please provide a justification of the date used.
DESIGNATION AS A QUALIFIED ANTI-TERRORISM TECHNOLOGY
Respond to all items in this section in one attachment to this application. Additional supporting material may be attached as an appendix to your application.
D9. Description of your Technology. One of the most important parts of the application process is defining the scope of your Technology. In this section, define your Technology with a sufficient degree of specificity. This description will serve as the basis for the Department’s analysis of your Technology for SAFETY Act purposes. The content of the response you provide in this section, together with any additional information you may be asked to provide, may be used to finalize the definition and scope of your Technology as it will appear in a Designation. Refer to the instructions for a more detailed example.
D10. Deployment and Operation. Describe the sequence of steps involved in deploying and operating your Technology. Provide sufficient detail to show that your company is capable of supplying your Technology. Be specific about all activities
such as the development, implementation, operation and management, etc. required to deploy your Technology.
D11. Readiness for Sale. How ready is your Technology to be sold and deployed? Please describe any modifications, adjustments, start-up time, hiring and vetting of personnel, building of manufacturing facilities, or other processes which might be required prior to a new deployment.
D12. Magnitude of Risk. Please provide an assessment of the magnitude of risk to the public from the type of terrorist activities your Technology would counter. Please describe, to the extent practicable, the scope of the injury, property or other damage, economic loss, loss of life, or other harm that could result from such terrorist activity. Please describe how the Technology has been deployed to date and how it can counter terrorist activities.
D13. Please describe how your plans for selling, deploying, or maintaining your Technology would be affected if the Department does not issue a SAFETY Act Designation for your Technology. Please describe how the Technology will be deployed in the future if SAFETY Act Designation is issued.
D14. Effectiveness and Utility. Provide information supporting the potential for your Technology to be effective in countering potential acts of terrorism. Please provide internal or external effectiveness tests or other information indicating the effectiveness of your Technology. This can include acceptance test data from a Government contracting action, penetration tests, case studies, pre and post- training testing, incident reports, customer feedback, or other relevant data or experience. As noted, acceptance of your Technology by a Government purchaser may be highly relevant and expedite approval of your application.
It is important that effectiveness data be in documented form if at all possible. You are responsible for providing all documentation in support of your application at the time of submittal, or to facilitate the transfer of any such information prior to submission. In the event that obtaining documentation is not possible and if POCs are provided as sources of information or testimonials, check below to indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate below specifically what information we should expect from each POC. Please see the Instructions for additional information.
 The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
D15. Include any other information the Department should consider in evaluating your Technology.
Documents in support of your Application should be uploaded as Attachments together with a separate numbered Table of Contents document. Please refer to the instructions regarding “Additional Attachments.” If POCs are provided as sources of information or testimonials, check below to indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate below what information we should expect from each POC.
 The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
D16. Insurance Data
D16.1. Please provide the information indicated below for any and all current liability insurance policies that are available to satisfy otherwise compensable third-party claims arising out of, relating to, or resulting from an act of terrorism were your Technology deployed in defense against, response to, or recovery from such act:
Primary named insured (as it appears on your insurance policy).
Additional named insured relevant to the Technology Sellers.
Type of policy (ies) (e.g., Comprehensive General Liability, Errors and Omissions, Aviation, Product Liability, SAFETY Act Liability, etc.)
Policy Dates. (Start and end)
Insurer.
Per-occurrence limits.1
Aggregate limits.

1 Please indicate whether the policy (ies) has a different limit or deductible/self-insured retention for terrorist acts than the general policy limit and, if so, provide both.
Annual Premium(s).2
Deductible(s) or Self-insured retentions.
Exclusions (please note and explain any pertinent insurance exclusions, cancellation terms, or limits that would potentially dilute or eliminate the availability of coverage under the policies identified in sub-paragraph “c” above).
Please describe the type and limits of terrorism coverage for this policy. Please elaborate on the applicability of the policies identified in sub- paragraph “c” to address the foreseeable risks associated with the deployment of the Technology, including those risks arising from the deployment of the Technology in advance of or response to an act of terrorism. Please also indicate whether the identified policy(ies) provides coverage under the Terrorism Risk Insurance Act (TRIA) of 2002, as amended, or other insurance policy(ies) provisions or endorsements.
l. Please describe whether the relevant policy(ies) covers SAFETY Act claims and whether the policy(ies) has a dedicated limit that applies to SAFETY Act claims only or has a shared limit (i.e., shared with non-SAFETY Act claims). Please indicate whether you have received a written interpretation letter from either the carrier or insurance broker indicating whether the policy covers SAFETY Act claims; if so, please provide a copy of such document.
D16.2. Unavailability of Insurance
If you do not currently carry insurance for the Technology that would be applicable in the event of an act of terrorism, please indicate the reasons. If you have attempted to purchase insurance but it is not available on the world market, please indicate the specific inquiries you have made. (You may submit written communications from insurance companies or brokers explaining why your Technology cannot be insured.)
If you have endeavored to purchase insurance but have not done so because you have concluded that the cost of insurance premiums would unreasonably distort the price of the Technology, please describe those efforts to find appropriate insurance and state why you have concluded that the cost of insurance for your Technology would unreasonably distort its sales price. In this context, you may need to provide an explanation with relevant documentation (e.g., insurance quotes with limits, premiums, exclusions, and other key items plus other relevant financial and market data). Note: The Department recognizes that the discussion of requisite insurance with an Applicant may require a number of

2 Insurance premium: If possible, please indicate what percentage of the premium is allotted to coverage for acts of terrorism.
communications while an application is pending. Thus, the question of whether a given premium would “distort the sales price” of a Technology might not arise when the application is submitted. If the question does arise later in the process, the Applicant may submit appropriate information at that time.
D16.3. Insurance Point of Contact
If POCs are provided as sources of information or testimonials, check below to indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate below what information we should expect from each POC.
 The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
The
POCs are
expecting contact
from DHS.
The information the
POC can
provide or
verify is:
D16.4. Revenue Projection
In order for us to determine the amount of insurance that would not unreasonably distort the sales price of your Technology, we need you to provide us with three (3)-year projected (prospective) revenue estimates for your Technology - all assuming that your Technology is approved under the SAFETY Act. The three-year period should include your current fiscal year, if incomplete, and two subsequent years.
If you do not have current year sales for your Technology, please provide us with three (3)-year projected revenue data.
The revenue data needs only to pertain to your Technology and the numbers need only be summarized data (that is, we do not require the revenue sources to be itemized). The revenue data should be matched with summarized cost data (e.g., cost of goods sold); as with the revenue data, we do not require breakdown of data by cost centers.
D16.5. Deployment. Please establish how the deployment of your Technology as an anti-terrorism technology would expose you to extraordinarily high liability and what this liability might be. This can be accomplished by developing a plausible scenario that establishes how the Technology could be the proximate cause of third-party claims in the event of an act of terrorism.
Please make the scenario and third-party liability claims specific to the deployment and use of your Technology.
D17. Financial Data
Certain financial information regarding your company and projected/prospective Technology revenue may be particularly relevant to the application process. This is particularly true when questions arise as to whether insurance costs for specified coverage limits unduly distort the price of your Technology. We may request additional financial information from the Applicant if necessary during the application process.
D17.1. You may provide a copy of the Seller’s financial statement for the most recent fiscal year. For public companies, the most recent SEC annual report (Form 10-K) and SEC quarterly report (Form 10-Q), together with any amendments thereto, should suffice. For non-publicly traded companies, you may choose to include the following information for the most recent fiscal year: income statement, statement of cash flow, and balance sheet as well as pro forma financial statement. OSAI will seek additional and more specific information only when necessary for a particular application.
ADDITIONAL ATTACHMENTS
Provide all supporting documentation. Please see the instructions for further information.
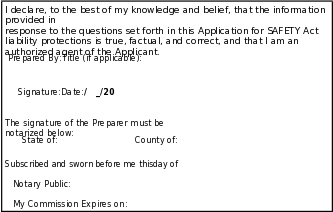
DECLARATION FOR WRITTEN SUBMISSIONS
Instructions for Completing Designation Application Form:
Application Type
Item D1. Type of Application
If you have not previously filed an application for SAFETY Act liability protections for this Technology or have not filed a request for Pre-Application Consultation, check “Initial Filing.”
If you have filed a request for Pre-Application Consultation regarding this Technology but have not previously filed an Application for SAFETY Act Designation as a Qualified Anti-Terrorism Technology (QATT), check the second box: “Application following a Pre-Application Consultation.”
If you have previously applied for SAFETY Act liability protections for this Technology, check the third box: “Resubmission of Previous Application.” This case applies if any previous applications for this Technology were withdrawn, found to be incomplete, or were declined. Previously incomplete or declined applications will not affect the evaluation of your current application; this information is requested for administrative and record-keeping purposes only.
If you are filing this form in order to apply for renewal of a Designation, check the fourth box: “Application for Renewal of Designation,” and enter the identification number of the Designation you are renewing as it appeared on your original notification. For renewal applications, you must complete all items but may respond with “No changes” to items that have not changed since your last application for Designation or approved Modification Notice. Wherever you have additional or revised information since your last Designation application or approved Modification Notice, complete that item as directed.
Expedited Review
Item D2. Request for Expedited Review
In its discretion, the Department may identify categories of anti-terrorism technologies for which expedited processing may be granted. For example, the Under Secretary may conduct expedited processing for applications that are the subject of a pending Federal, State, or local procurement, which address a particular threat involving particular types of anti-terrorism technologies, or for other reasons. If you are requesting an expedited review, please specify the appropriate basis for expedited treatment of your application.
If your Technology is the subject of a pending Government procurement or if you are planning to submit a proposal for a procurement decision in the near future, provide the following information to the extent available:
Name of procuring organization;
Contact information for relevant Government procurement officials;
Related Request for Proposal (RFP) number or other official identifier of the procurement; and
Upcoming deadlines relating to the procurement (e.g., submission deadline, decision/contract award, etc.).
If your request to expedite falls under a published DHS Notice of Expedited Processing, check the appropriate box and follow the published instructions from the announcement.
If your request to expedite is not related to procurement, please provide the basis for your request and any available supporting information.
Registration Information
Item D3. Registration Information
Please check the appropriate box relating to your registration status.
Item D3.1. Name of Seller/Applicant
Enter your Seller name as listed on your registration form.
Overview of the Anti-Terrorism Technology Item D4. Non-Proprietary Summary
Item D4.1. If this is the first application for this Technology, assign a name to your Technology. This is the name that will appear on any Designation that may be issued.
If you are applying for renewal of an existing Designation, use the name that appears on your most recent Certificate of Designation or Modification Notice.
Item D4.2. The purpose of this item is to help the Department recognize potential conflicts of interest and to avoid disclosing your application information to inappropriate evaluators. The Department is committed to protecting your sensitive business data from improper disclosure.
Provide a brief description of your company, including place of incorporation, a description of your business, and the Technology that is the subject of the Application. When describing your company, focus on identifying any affiliates that will be involved with your Technology (e.g., parent companies, subsidiaries, joint venture partners, holding companies, etc.). When describing your Technology, focus on providing information that will help the Department identify which Subject Matter Experts (SMEs) would be best qualified to evaluate your Technology. This description should be no more than two sentences long and should be appropriate for placement on a public Web site if your application for SAFETY Act coverage is approved.
The purpose of the company description and Technology description is to help the Department recognize potential conflicts of interest and avoid disclosing your application information to inappropriate evaluators. The Department is committed to protecting your sensitive business data from improper disclosure. Do not include any sensitive or proprietary information in this summary. If you wish to include information on substantially similar QATTs or provide information regarding who your major competitors are with respect to the subject Technology, you may do so.
Item D5. Nature of Your Technology
Please briefly describe the nature of your Technology in two pages or less. The SAFETY Act applies to a broad range of anti-terrorism technologies. In your response to the question, please describe whether your application is for an anti- terrorism product, service, combination of products and services, information technology, or some other form of intellectual property. If your Technology is a product or device, please describe the Technology in detail, including its principal elements, sub-systems, and components. If your Technology is a service, please describe the nature of the service, the actions, and associated services, activities, planning, training, and/or expertise involved in providing the service and how the service is designed to counter terrorist threats. If your Technology is an “integration” of various products, services, or legacy systems indicate how the Technology will integrate the various component parts.
Item D6. Past Sales and Ongoing Procurements
If POCs are provided as sources of information or testimonials, please indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate what information we should expect from each POC.
Item D6.1. What sales of your Technology have you made to date? Identify a representative sale and approximate date for each category that applies. You may add additional attachments as necessary. Please also specify anticipated sales of your Technology.
Note: It may be very important and could significantly expedite your application if your Technology has been acquired or used (or is subject to an ongoing procurement) by the military, a Federal Government agency, or a State, local, or foreign governmental entity.
Item D6.2. For each Federal, State, or local Government agency that has purchased your Technology, provide contact information for one or two points of contact in an attachment. For non-Government sales, provide one Point of Contact. For each Federal acquisition, attach a copy of any Request for Proposals or Broad Agency Announcements that led to the award and a copy of your final proposal and Statement of Work.
For each customer, please indicate whether:
The Technology has been fully deployed.
The Technology is in the process of being deployed.
The Technology has been purchased, but deployment has not yet begun.
The deployment is conditional on the Technology earning QATT status.
The Department will assume that any Point of Contact you provide has been given permission to be contacted by DHS regarding your application.
If POCs are provided, please be advised that:.
The SAFETY Act may make contact with persons that you list as having information to support the claims in your Application; however it is your responsibility to make sure that you have provided all information to support your Application at the time of submission. We suggest that you obtain written testimonials from your customers.
If you choose to supply points of contact because you believe that third- parties will be able to provide additional supporting information for which you do not have access (such as for example, classified reports, audits, vulnerability assessments, or other reports or data), remember to:
Be sure that the contact information you provide to us is current.
Notify your references that you have submitted a SAFETY Act application and that we may contact them.
Make sure that you are giving us the contact that will be able to provide the best information on the nature of the past sale or deployment, and on how your technology actually worked.
You may also supply contact information for third-parties, e.g., government officials, who might supply customer testimonials. These individuals should be able to supply actual knowledge of how your technology works and of its utility. We suggest that you obtain this information in writing.
For past sales, provide the contact information for any purchase referenced in D6.
For procurements, list the name and contact information for the procurement officer or similar person in charge of the contract, proposal, or Request for Proposal.
Item D6.3. Please provide information, if applicable, regarding how the United States Government or any State, local, or foreign Government has used or is using your Technology. You may also include information relating to your Technology’s use by other entities and commercial deployments undertaken in coordination or conjunction with Federal, State, local, or foreign Governments.
Item D6.4. Please identify any determination made by Federal, State, or local Government officials that your Technology is effective and appropriate for the
purpose of countering terrorism. Such determinations may have been made as part of Government procurement, licensing action, or in other contexts. Note: It may be very important and could significantly expedite your application if your Technology has been acquired or used (or is subject to an ongoing procurement) by the military, a Federal Government agency, or a State, local, or foreign governmental entity. As appropriate, you should identify why the previously examined Technology is appropriate for countering acts of terrorism or limiting the harm such acts might otherwise cause.
Item D7. Seller
In certain instances, multiple corporate entities may appropriately be identified as a Seller of the subject Technology. For instance, the Seller of the QATT could include a parent company as well as subsidiaries or other affiliates. Your response will be used to properly identify the Seller(s) of the QATT. If you would like multiple entities to be considered a Seller of the QATT, please clearly and precisely identify each of these firms and identify their respective place of incorporation.
Item D8. Earliest Date of Sale
This information will be used to specify the earliest date of sale of the QATT to which the Designation shall apply. Please provide information on the significance of this date. If the date is more than five years prior to the date of application, please explain how you know your Technology has not significantly changed in that time frame.
Designation as a QATT
Under the SAFETY Act, the Secretary of the Department of Homeland Security will consider enumerated, non-exclusive criteria in evaluating a Technology for potential Designation as a QATT. The Act gives the Secretary discretion in determining whether to designate a particular technology as a QATT.
This section of the Application requests information that is necessary to evaluate your Technology. Attach your responses to this section as one attachment. Not all questions will be applicable to all types of technology. If a particular request or question does not seem relevant to your Technology, do not leave a question blank or merely refer to a previous response. Please contact the SAFETY Act Helpdesk to request clarification.
This section must be presented in a narrative format, referring to each section below. The ATT Details section should be written so that the reader may clearly understand what your Technology is, what it does, and how it operates. The narrative sections should consist of your claims about the capabilities, and effectiveness of your Technology in an anti-terrorism context. It is important that all of your claims are supported by relevant documentation in some manner. Depending on the nature of your technology, e.g., product vs. service, that support would normally include such items as case examples, test data, audits, assessments, reports, specification sheets,
operating manuals, instructors manuals, performance reports, procedural manuals, and the like. It is vital that you cross reference the supporting documentation to each claim you make in order that our reviewers understand what material you wish us to evaluate. You should also provide a Table of Contents listing as a separate attachment which itself, lists your numbered attachments or exhibits.
Item D9. Description of your Technology
One of the most important parts of the application process is precisely defining the scope of your Technology for evaluation and Designation. In order for the Secretary to issue liability protections to your Technology, you must define with specificity what that Technology is – that is, what you provide to your customers when you sell that Technology, what it does, how it works, and what aspects of it are invariable from deployment to the next. Note: embellishments, marketing materials, and elements which cannot be substantiated in the rest of the application should not be included. This Description is an expansion of that which you provided in Items D.4 and D.5, and will encompass the legal description of your Technology for any award the Department may issue. In response to this section, include the following:
Company name, business structure, additional sellers, and states of incorporation, as applicable;
Name of the Technology;
Nature of the Technology;
Purpose or intent of the Technology;
Description of how the Technology works;
A statement of where the Technology is intended to be utilized, e.g., in the private sector, for the Federal government, for the military, etc.;
A brief description (no more than two lines) of the type of terrorist attacks or attempted terrorism acts the Technology is expected to counter; and,
The principal elements, systems, or components provided to customers (indicating, which components, if any, are optional)
The above elements as you provided in your Application will be translated into a concise description by the Office of SAFETY Act Implementation, as in the following example:
(Name of company, and any subsidiaries), a (State of Incorporation) company, provides the (Name of technology) which is designed to (Purpose of the technology). (Name of Technology) e.g., does this by (Briefly describe how it works) for ( Place of deployment or type of customer). The Technology is used for the following anti-terror purpose(s) (type of threat). The Technology includes the following elements:
(list e.g., hardware and software )
(list – e.g., integration services)
(list- e.g., training and consultation)
Note that for each component listed in your Technical Description, you must provide support of capability and effectiveness. Your description should answer the following questions:
How and where may your Technology be used? If your Technology is a device, address what training, if any, is necessary to use your Technology. If your Technology is a service, describe what types of facilities you might serve and how your Technology is tailored to providing anti-terrorism services at those locations.
Scope of your Technology: Briefly list the underlying principles or properties that allow your Technology to perform its functions and achieve its purposes. If your Technology consists of devices, briefly explain the operational principles of those devices. If your Technology consists of services, explain how those services are implemented to ensure consistent quality wherever they are delivered and whether these services conform to recognized industry standards. If your Technology consists of software, explain the key features and algorithms. If your Technology consists of some other kind of product, briefly explain how you produce that product. This information will help the Department understand the precise scope of the Technology for which you are applying for SAFETY Act coverage. If your Technology Description encompasses too broad a scope, e.g., in areas of deployment or in threats countered, you may be asked to provide separate Applications.
What are the important elements that make up your Technology? That is, what are the component processes, devices, software, or other contributing activities and technologies that will be included in your specification? How are they defined or delineated? Be aware that any ancillary components of your Technology that are identified in your specification (e.g., manuals, training, maintenance, etc.) should be supported in subsequent sections by sufficient information to evaluate them. What parts of your business, if any, are explicitly not included in this specification for purposes of this application?
Examples of component systems and activities of your Technology might include:
Equipment
Software
Software design
Personnel training and qualifications
Staffing
Algorithms
Consulting services
Systems integration services
Decision support systems or services
Maintenance contracts
Periodic upgrades, post-deployment reviews
Testing services
Quality control features
If your Technology is primarily service-based, focus on describing the various activities and sub-processes that contribute to the overall delivery of your service(s). This information will help the Department understand the precise scope of your Technology.
In addition to describing what you do, you should also briefly describe any elements, processes, or activities that complement or interact with your Technology but that are not specifically part of the Technology in this application and may be supplied by the end-user. These might include other technologies you sell, activities performed by your customers, technologies provided by other vendors, or parts of the public infrastructure. This information will help the Department understand the precise scope of Technology you are establishing in this specification. If your Technology helps to integrate new components with legacy systems, please indicate that.
After developing this description, make sure that you refer back to it when developing support for Items D.10 and D.14.
Item D10. Deployment and Operation
Describe the steps involved in the course of developing, producing and providing your Technology to a customer. Using the Technology Description developed above; you should provided documented support of your capability to provide all elements of your Technology in these areas.
It is useful to begin by describing the sequence of steps involved in providing your Technology to a customer, from initial contact to final deployment. Focus your description on the process of producing and deploying your Technology, as opposed to the end result or the nature of any specific tangible deliverable. Where possible, include the estimated time required for each activity or step.
If your Technology involves physical products, your discussion might include elements such as:
Manufacturing capabilities (where will the Technology be manufactured, are facilities in place, is there a manufacturing plan in place?)
Production, including quality assurance, factory acceptance tests, manufacturing standards, and the like.
Installation and configuration plans, to include site acceptance tests
Operation plans, operator instructions, and the like
Training, including any user manuals or terms of use
Maintenance and any maintenance records
Monitoring
Upgrade policies
Warranties and service contracts
Post-deployment quality control
If your Technology includes software or information technology, please include information such as:
Software lifecycle development plans, including any verification, validation, and accreditation (VV&A)
Software upgrade policies
Network architecture information
Network security information
Network stress testing
Customer input into user access
If your Technology involves services, your discussion might include (as relevant):
Pre-deployment work such as, Customer requirements analysis or site surveys Staffing requirements, documentation of expertise, hiring and vetting policies
Operational plans, policies and procedures, including items such as: post orders and operational manuals
Training, including: curriculum development, trainer’s notes, handouts, testing materials, and presentation materials
Post-delivery support and procedures
Administrative and operational policy and procedure Documents
Quality Control, to include: internal or independent audits, managerial oversight at the local and corporate level, policy revisions, learned lessons, etc.
Please see “Additional Attachments” below for instructions on supporting document and classified materials submission.
Item D11. Readiness for Sale
If your Technology is not yet being marketed, estimate the time before your Technology will be available for sale or will be sold at your planned maximum rate. You should include any anticipated delays due to funding, required marketing, required licenses or certifications, staffing, sub-contractor delays, etc.
If your Technology is already deployed, describe the deployments. Your description should include the circumstances and the nature of the deployment of your Technology. Provide sufficient information about the scope of the deployment that addresses the following questions: (1) has it already been deployed? (2) Is it being deployed? (3) Has it been purchased for deployment in the future? Information
could also include the length of the deployment, the purpose of the deployment (testing versus general use), and the types of customers using the Technology.
Your response should include an estimate of the time frame before your Technology will be ready for sale or the time required for standing up a new deployment. This should include a discussion of your recruitment, hiring, screening and training procedures, as well as any procedures you use to retain your personnel. Relevant policies should be uploaded as Attachments. Please reference all Attachments and provide a Table of Contents.
Item D12. Magnitude of Risk
Please provide an assessment of the magnitude of risk to the public from the type of terrorist activities your Technology would counter. Your response should identify the types or categories of potential terrorist activities your Technology is intended to address. Your response should also present, to the extent practicable, estimates of the scope of the injury, property or other damage, economic loss, loss of life, or other harm, including financial harm, that could result from such terrorist activity.
Additionally, please describe how the Technology has been deployed to date to counter such terrorist threats.
Item D13. Impact of SAFETY Act Designation
Please describe how your plans for selling or deploying your Technology would be affected should the SAFETY Act’s system of risk and litigation management not be made available. Please describe how the Technology will be deployed in the future if SAFETY Act Designation is issued. Within the response, please address how current and future deployments of your Technology would be affected without SAFETY Act protections. To the extent possible, include the likely effects of the excessive costs of insurance on the price of the product, and the possible consequences thereof on development, marketing, manufacture, qualification, sale, transportation, use, operation, and support of the Technology.
Item D14. Effectiveness and Utility
The information you provide here should include information supporting your belief that your Technology can be a valuable counter terrorism tool. The kind of documentation you provide will depend on the nature of your Technology. You should support each element, sub-component, or model listed in the Technology Description which you provided in response to Item D.9. If you apply the same supporting information to multiple elements, sub-components, or models, please indicate why this is reasonable.
If your Technology is primarily a device or software product, your documentation should emphasize available developmental and operational test data that indicate the likely operating performance of that device or software. This could include performance in past deployments, independent test results, Government licenses or certifications, field tests (e.g. performance against simulated attacks), internal test
data, customer studies, scientific studies of the techniques involved, industry reports, Government or military publications, or any other documentation or experience that suggests or supports the potential usefulness of your Technology. Please attach copies of any such reports, publications, or evidence by using the additional attachments sections that would facilitate analysis and evaluation of your Technology by Subject Matter Experts (SMEs). Please reference all attachments in your response and provide a Table of Contents in D.15.
If your Technology is primarily a service, your documentation should emphasize the quality of the process whereby that service is delivered and should include any available evidence of successful past deployments of a similar nature. In particular, you should provide or cite information that documents any of the following:
The results of independent and internal company audits
The results of operational or tabletop exercises pertaining to this Technology
Case histories of successful deployments or specific incidents indicating effectiveness
The repeatability of your processes for providing a core set of services prior to any site or customer specific customization.
Your methods for monitoring your adherence to your processes and to industry standards, benchmarks or best practices.
The Department will not ordinarily conduct tests of your Technology for purposes of SAFETY Act evaluation or compare your Technology directly to other similar technologies. Reviewers will evaluate your Technology against the statutory criteria for Designation primarily on the basis of the information you provide. Accordingly, the information you provide in response to this question should be as comprehensive and thorough as possible. It may be very important and could significantly expedite your application if your Technology has been acquired or used (or is subject to an ongoing procurement) by the military, a Federal Government agency, or a State or local governmental entity. Procurements of your Technology by a foreign Government may be relevant.
Please provide an overview narrative relative to the effectiveness of your Technology, including references and summaries of supporting documentation. If you reference any material that is not publicly available, it should be included as an attachment to your application. If you refer to information provided elsewhere in your application, cite it by internal title, item number, and the name of the attachment. Even though your entire application will be treated as confidential, you may (but are not required to) specially mark those portions of your application which contain proprietary and/or business confidential information.
Please see “Additional Attachments” below for instructions on supporting documents and classified materials submission.
If POCs are provided as sources of information or testimonials, please indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, please be advised that:
The SAFETY Act may make contact with persons that you list as having information to support the claims in your Application; however it is your responsibility to make sure that you have provided all information to support your Application at the time of submission. Do not simply include a listing of your customers for DHS to contact. We suggest that you obtain written testimonials from your customers.
If you believe that third-parties will be able to provide additional supporting information for which you do not have access (such as for example, classified reports, audits, vulnerability assessments, or other reports or data), remember to:
Be sure that the contact information you provide to us is current.
Notify your references that you have submitted a SAFETY Act application and that we may contact them.
Make sure that you are giving us the contact that will be able to provide the best information on the nature of the past sale or deployment, and on how your technology actually worked.
You may also supply contact information for third-parties, e.g., government officials, who might supply customer testimonials. These individuals should be able to supply actual knowledge of how your technology works and of its utility. We suggest that you obtain this information in writing.
For past sales, provide the contact information for any purchase referenced in D6.
For procurements, list the name and contact information for the procurement officer or similar person in charge of the contract, proposal, or Request for Proposal.
Item D15. Summary of QATT Qualifications
If you wish, you may use this item to summarize in broad terms why you believe your Technology qualifies for SAFETY Act Designation. Please provide whatever additional information that would be helpful to the Department in analyzing and evaluating your Technology. You may refer to the specific criteria of the Act, or suggest other relevant criteria, as you see fit. If you are providing attachments, please provide a Table of Contents.
If POCs are provided as sources of information or testimonials, please indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate what information we should expect from each POC.
Item D16. Insurance Data
Document any and all current insurance coverage that would be available to satisfy otherwise compensable third-party claims arising out of, relating to, or resulting from an act of terrorism were your Technology deployed in defense against, response to, or recovery from such an act and found to have caused harm. Please state whether such policy includes Terrorism Risk Insurance Act (TRIA) coverage, as amended, or other insurance policy(ies) provisions or endorsements that cover acts of terrorism. Please specify any relevant exclusions or cancellation provisions that would limit the availability of the current policies to satisfy third-party claims. Please also ensure that the insurance coverage for all of the Sellers listed in D7., is contained in the answers to the items below. In doing so, please be certain to specify whether the Seller(s) is/are the primary insured or an additional insured.
If POCs are provided as sources of information or testimonials, check below to indicate that you have contacted them and that they are expecting to hear from DHS related to your Technology. Also, indicate below what information we should expect from each POC.
Item D16.1. Current Insurance
For item 16.1a, provide the name of the company identified as the primary insured for the relevant current policy. If you are an additional insured instead of the primary policy holder, please identify the primary insured and each other firm identified as an additional named insured in item 16.1.b.
In item 16.1.k., specify the type of terrorism coverage provided under the referenced policy(ies) (e.g., Terrorism Risk Insurance Extension Act, as amended, other coverage, no terrorism exclusion). Please specify the overall and per-occurrence limits that would apply to the terrorism coverage.
Item D16.2. Unavailability of Insurance
The SAFETY Act provides that a Seller may not be required “to obtain liability insurance of more than the maximum amount of liability insurance reasonably available from private sources on the world market at prices and terms that will not unreasonably distort the sale price of Seller’s anti-terrorism technologies.” If you are unable to obtain appropriate insurance, please provide information concerning your attempts to obtain insurance coverage for your Technology (e.g., written communications from insurance companies or brokers explaining why your Technology cannot be insured). If insurance is available for terrorism events but at rates which would distort the sales price of your Technology, document the prices of that insurance and provide the relevant information to support how this would affect the price of your Technology. You may wish to contact OSAI with questions concerning what information would be most helpful to provide in response to this item. Note: The Department recognizes that the discussion of requisite insurance with an Applicant may require a number of communications while an application is
pending. Thus, the question of whether a given premium would “distort the sales price” of a Technology might not arise when the Application is submitted. If the question does arise later in the process, the Applicant may submit appropriate information at that time.
Item D16.3. Insurance Point of Contact
Insurance Point of Contact. Provide a point of contact, including telephone number and e-mail address for someone authorized to discuss your company’s insurance information with the Department. This point of contact may be the same person identified in your registration statement and may be your counsel, insurance expert, or any other person with appropriate information.
Item D16.4. Revenue Projections
Please provide us with three (3)-year projected (prospective) revenue data for your Technology. The three-year period should include the current fiscal year, if incomplete, and two subsequent years (best estimate). If you do not have current year sales data for your Technology, please provide us with best estimate projections for the three years following the launch of the Technology. The SAFETY Act requires Sellers of anti-terrorism technologies to obtain liability insurance of such types and in such amounts to satisfy otherwise compensable third-party claims arising out of, relating to, or resulting from an act of terrorism when a Technology has been deployed in defense against, response to, or recovery from an act of terrorism.
Technology revenue projections are of particular relevance in the application process. This is true when questions arise as to whether insurance costs unduly distort the price of your Technology.
Item D16.5. Deployment
Your response should identify the types or categories of potential terrorist activities your Technology is intended to address. Your response should also present, to the extent practicable, estimates of the scope of damage, loss of life, or other harm, including financial harm, that could result from such terrorist activity. As noted in the question, describe in a brief statement how the deployment of your Technology as an anti-terrorism technology could expose your company to extraordinarily large or unquantifiable potential third-party liability, and the potential range of the liability (in
U.S. dollars). We have found that use of a brief and concise scenario is a good means to indicate how your Technology could expose you to third-party claims in the event of an act of terrorism.
Item D17. Financial Data
Certain financial data may be used in the process for analyzing the appropriate amount of insurance coverage for your particular Technology. This is particularly true when questions arise as to whether insurance costs unduly distort the price of your Technology. Accordingly, you may be asked to provide certain financial data to
OSAI as part of your application. If this is the case, OSAI will not demand financial information when it is not necessary for a particular application, and will not disclose sensitive or proprietary information outside the application process. Applicants may wish to provide financial data relating exclusively to the Technology.
Item D17.1. It may be helpful to attach your latest financial statement. If you are a public company, your latest SEC 10-K annual report and SEC 10-Q quarterly report, together with any amendments thereto, should suffice. If your company is not publicly traded, you may choose to include the following information for the most recent fiscal year: income statement, statement of cash flow, and balance sheet as well as pro-forma financial statement. OSAI will seek additional and more specific information only when necessary for a particular application.
Additional Attachments
In the process of answering the questions above, you might find it useful to attach additional documents in support of your answers. These items can be included in your application by using the “Additional Attachments” feature. When answering the items above, it is appropriate to refer to attachments by name and or number.
Examples of common attachments might include, but are not limited to, the following: test reports demonstrating the effectiveness of the Technology, operating manuals, training manuals, project/program management plans, quality assurance plans, quality control plans, copies of company certifications, results from pilot studies, testimonials from customers, and warranties.
Submitting Documents as Attachments:
Documents in support of your Application should be uploaded as Attachments together with a separate numbered Table of Contents document. Attachments should be individually labeled and or otherwise clearly identified. For ease of use, we prefer that documents are uploaded individually, rather than in a “Zip” file. Do not submit the ATT Details Narrative document in write-protected format since that information must be accessible to us for use in the creation of OSAI Program documentation. Ideally, attachments should be cross referenced in your narrative response, with clear indications of the purpose of the Attachment. It is usually unnecessary to upload third-party material, such as government training presentations, regulations or standards documents. You may refer to these documents in your narrative and provide an open-source link. For additional assistance in uploading documentation, or for further questions, please call the SAFETY Act Help Desk.
Submitting classified or sensitive data or information:
In cases where the effectiveness data, e.g., audits or testing, that you wish to have evaluated is classified or sensitive and is held by a third party; the Department will attempt to assist you in obtaining this information, however, you MUST facilitate the transfer of that data to the SAFETY Act office PRIOR to the submission of your
Application. This means that you must notify the custodian of records for your customer of your Application to the SAFETY Act and that Department requires access to those records. Once you have completed this step, you must provide the Department with the name and contact information of the holder of these records. When a date has been set for the transfer of information, you may submit your Application. For further assistance call the SAFETY Act Help Desk.
Declaration for Written Submissions
An authorized agent of the Applicant must, in the presence of a Notary, sign and date this form before submitting it to OSAI. For electronic or Web submissions, follow the instructions provided at safetyact.gov.
| File Type | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File Title | Microsoft Word - 10008_Application_for_SAFETY_Act_Designation.doc |
| Author | RCNelson |
| File Modified | 0000-00-00 |
| File Created | 2025-02-13 |
© 2026 OMB.report | Privacy Policy